October 1996
| Foundation for Intelligent Physical Agents | |
| Tokyo, Japan October 1996 | F I P A |
FIPA's First Call for Proposals
( CFP1 )
Executive summary
The First FIPA Call for Proposals is an invitation to submit proposals for technologies usable in a selected number of emerging agent-based applications and services, specifically in the following four categories:
These proposed technologies are intended to be utilised in the development of specifications of component technologies that may be used by application developers for first implementations of the aforementioned application areas. The time scale of specification development is 1997.
Deadline for proposal submission is 10 January 1997 for consideration at the fourth FIPA meeting on 20-24 January 1997.
Click here for detailed information on how to submit.
Table of Contents
- 4.1. Rationale
- 4.2. Personal Assistant
- 4.2.1. Rationale
- 4.2.2. Description and Reference Model
- 4.3.1. Rationale
- 4.3.2. Description and Reference Model
- 4.4.1. Rationale
- 4.4.2. Description and reference model
- 4.5.1. Rationale
- 4.5.2. Description and Reference Model
- 5.1. Introduction
- 5.2. Agent management
- 5.2.1. Introduction
- 5.2.2. Agent Interface Description Language (AIDL)
- 5.2.3. Agent Security
- 5.2.4. Agent Lifecycle Model
- 5.3.1. Introduction
- 5.3.2. Message types
- 5.3.3. Message contents
- 5.3.4. Interaction protocols
- 5.3.5. Enabling technologies
- 5.4.1. Introduction
- 5.4.2. Attachment to external software, applications and services
- 5.4.3. Attachment to internal components
- 5.4.4. Enabling Technologies
- 6.1. Introduction
- 6.2. Personal Assistant
- 6.3. Personal Travel Assistance
- 6.4. Audio/Visual Entertainment and Broadcasting
- 6.4.1. Overview
- 6.4.2. Application: System Configuration and Capability
1. Introduction
Rapid developments in agent technology are creating conditions for the deployment of applications, services, and products that are attractive to users by virtue of their ability to offer improved functionalities compared to those of existing technologies. The current environment is one in which agent-based systems are designed and deployed on an ad-hoc basis. FIPA has been established to promote a larger deployment of interoperable agent systems. This is accomplished through the standardisation of component technologies that may be used by application developers across a wide variety of applications and providing a high level of interoperability across those applications.
Although there is a large number of applications that can benefit from agent technologies, addressing too many of them simultaneously in this early stage would be impractical. Therefore this Call for Proposals concentrates on a subset of services and applications with a first set of functionalities, in the areas of Personal Assistant, Personal Travel Assistance, Audio-Visual Entertainment and Broadcasting, and Network Provisioning and Management.
It should be realised, however, that FIPA is not attempting to specify applications but only uses models of existing or possible applications to identify and assist in specifying the agent component technologies required to implement them. This enables the assembly of applications which would not have otherwise been feasible without standardization.
Those intending to submit a proposal(s) should consult Chapter 7 of this Call for Proposals.
FIPA is concerned only with specifications of interfaces and protocols associated with component technologies, but it may nevertheless be necessary to be made aware of certain technological solutions and to understand their technical operations sufficiently for the purpose of accurately capturing their operation as a 'black box' specification.
It is the intention to have the FIPA specifications considered by formal standards bodies for endorsement wherever appropriate.
A healthy cross-industry response from interested parties will ensure that the technologies will be adopted which will be in support of the interoperable agent based applications.
FIPA meetings may be attended by member companies only, however, companies who have submitted proposals but are not FIPA members will be allowed and invited to attend the January 1997 meeting for the purpose of introducing their proposals.
FIPA is an open organization and expressly encourages any entity to become a member. Inquiries on membership should be directed to the address given in Chapter 7.
Application for membership to FIPA can be found on the FIPA homepage
While FIPA plans to have a series of Calls for Proposals concerning different aspects of agent technology, there is currently no plan to have a further call on the specific subject of this document. Therefore proponents should ensure that their contributions are submitted during this opportunity and comply with the deadlines specified. However, FIPA recognizes the evolution of technology and plans to issue further Calls for Proposals in order to:
A first draft of the FIPA specifications, based on the submissions received, will be produced
at the 5th meeting in April 1997. A second draft will be produced at the 6th meeting in July
1997 and a final specification approved and issued at its 7th meeting in October 1997. While
FIPA intends to work by consensus, this very aggressive schedule may require the use of
membership voting. The FIPA governing statutes are available on the FIPA Homepage.
2. Structure of this Call for Proposals
Chapter 3 of this document describes the nature of FIPA specification. Unlike other bodies which issue specifications targeted to specific applications, FIPA only uses applications for the purpose of identifying requirements for component technologies ("tools" in FIPA language) that are needed to implement the applications. This approach makes it possible to use standardised tools for building applications serving different needs with a high degree of interoperability. This point must be borne in mind to understand the structure of the document.
Chapter 4 provides a detailed explanation of the four target applications, as they can be implemented using agents.
Chapter 5 contains the list of component technologies target of this Call. This has been produced from an analysis of the requirements from the selected applications.
Chapter 6 provides a description of possible implementations of the four selected applications
as a result of the specification of agent component technologies listed in Chapter 5.
3. Nature of FIPA specifications
Promotion of the development and specification of agent component technologies is the task of the Foundation for Intelligent Physical Agents (FIPA). The following are the main features of FIPA's specifications
4. Target applications of this Call for Proposals
4.1 Rationale
Agents here mean relatively autonomous units that can adapt to, and interact with, the environment (both software and hardware) that they live in. Some functionalities of the applications can also be supported with non-agent technology. FIPA believes, however, that the use of agent technology and inter-agent communication protocols provides an effective means for building large (i.e. commercial) systems of services in a modular way by producing "plug-in" software, and painless extension of capabilities.
The use of rational agents allows the definition of intelligent personal assistants, brokers and more generally of "combination of services". The benefit we can expect from rational agents is the ability to develop more and more complex services, far beyond existing technology possibilities.
A small number of application areas for the use of agent technologies has been selected as
example applications. This allows FIPA to address relevant applications that are interesting in
the business world and not only to agent-technology researchers. It also allows FIPA to
select and focus on relevant technologies that are available, now or in the near future, in the
research and development community that can be put together to build the first FIPA
standards set.
4.2.1 Rationale
One central class of intelligent agents is that of a personal assistant (PA) or intelligent personal agent. A personal assistant is a software agent that acts semi-autonomously for and on behalf of a user, modelling the interest of the user and provide services to user or other people/PAs as and when required.
The notion of a personal assistant is very open-ended. There are many, many internal and external functions/services that can and will be used to provide and extend a Personal Assistant's basic functionalities. In fact, such openness to new services is a critical requirement where interoperability of PAís functions/services is desirable.
The examples of such functions/services are to include: to communicate with the user to help
managing his/her directories and diaries (e.g., meeting scheduling), filtering and sorting mails
(e.g., electronics mails), locating and delivering (multimedia) information, recommending
movies, purchasing desired items, planning travel, etc. The other FIPA application scenarios -
especially the Personal Travel Assistance and the Audio-Visual Entertainment and
Broadcasting - also include this notion of end-user personal assistance, but this application
focuses on the generic requirements for personal assistant.
4.1.2 Description and Reference Model
A personal assistant comprises:
The scope of this composite is limited to the tasks which are given by the user as goals and preferences for behaviour. Other agents will also exist and interact with the personal assistant, but such other agents will not tend to represent particular user's preferences, or access authority and other differentiators. The composite is visualised in the following reference model.
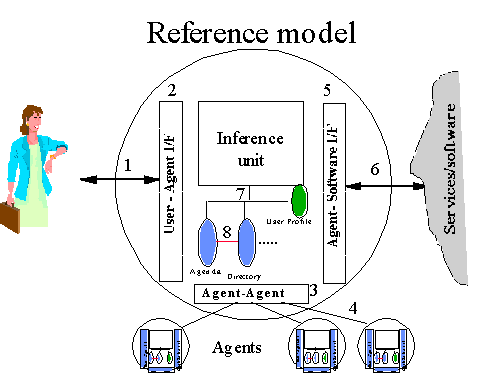
Fig. 1 - Reference model for Personal Assistant.
The reference model includes the following interfaces/protocols of interaction that are candidates for standardisation.
Multi-modality is the ultimate goal for human-agent interfaces. As a user interacts with a real personal assistant, he/she can speak face-to-face with the assistant or over the phone. Obviously, unconstrained natural language comprehension is also desirable. However, as first steps toward this general goal, "multi-modal" interaction is taken not as requirement for all agents to support all modalities, but merely that any single application should be able to select the one or more modalities required for the application. The composition of the personal assistant should be media-independent in order to allow for this choice, and otherwise provide the multi-modal conversions required such as converting text to speech in order to pass information over the phone.
In order to provide some concrete examples, the following scenarios serve to expose the basic PAís functions/services needed.
Directory Services
One of the basic functions of a PA is the management of the user's directory. This directory includes other people's/organisations' telephone numbers, addresses and personal and useful information about them. This information facilitates responses the PA may provide to user's needs in an intelligent way, based on the context of the request. For example, if the user asks to call an organisation and the PA by reference to the opening and closing time notices that the call cannot be made, it will suggest alternative actions by inferring the user's possible intentions on the basis of the services provided by the organisation. A request for a call to a specific travel agency out of opening hours may result in the PA suggesting contacting a 24-hour call centre of an airline company.
Meeting Scheduling Services
The personal agent includes, obviously, a calendar facility, that among other things can be used for scheduling of meetings, and negotiation with users and other agents. The functionality includes:
Information Management Services
This is a very large and nebulous set of tasks but also addresses one of the most critical needs for intelligent personal agents. Most professionals are now inundated with too many sources of information, generally this is called "information overload". An agent can serve to semi-autonomously filter, sort, or otherwise respond to all these sources to help off-load some of the more mundane tasks these professionals now must do themselves. Such task include:
A key aspect of such information management is not just filtering out the low priority information, but also providing the timely delivery of high priority items - anywhere, anytime, anyhow. Such delivery is dependent on the user's location, media/equipment limitations, and user preferences. For instance, an agent can be instructed to deliver important e-mail to an end-user even if the user only has a mobile phone by converting the text to speech. Of course, this same text-to-speech delivery of e-mail over a mobile phone can be applied to any text-based information source such as NNTP news, stock quotes, etc. Furthermore, given the cost of mobile phone connectivity, other technologies such as text summarisation can be employed, for most efficient delivery of the users time and cost. The provision of such summarisation and media to media transformation could be provided, for example, via external services.
Even under the most constrained situations, such as the user only having a pager, a personal assistant can at least notify the user about the existence and accessibility of an important new multimedia document. Even though the pager device cannot deliver the information, the personal assistant can notify the user of the appropriate equipment in the locality of the user that is available where the multimedia document could/would be sent to.
A less well-developed but equally important aspect of information management is the personal storage and retrieval of information. Even personal computer storage is becoming difficult to manage. Files are often duplicated, directory structures are haphazard, and the file systems themselves does not provide rich indexing and content search facilities. Within an intelligent personal agent, such functions also take the metaphorical role of a personal assistant; like a personal secretary, it can be asked to file and retrieve documents or even isolated bits of information.
As an example of a desired service provided by a PA we can mention Travel Planning service.
Travel Planning Service
The personal agent can assist in planning the userís trip. To achieve that the PA interacts with the user, other agents and external directory services (such as yellow pages) and provides an appropriate plan of an intended trip and other guidance services. See Personal Travel Assistance Application in this call.
4.3 Personal Travel Assistance
4.3.1 Rationale
A wide variety of travel related services are becoming increasingly available through electronic means. There is a need for convenient and ready access to these services, in particular for travelers. This presents a prime example to showcase the benefits of agent technology. Agents operating on behalf of their users can provide assistance in the pre-trip planning phase, as well as during the on-trip execution phase of a trip. A system supporting these services is called a PTA (Personal Travel Assistance) system.
In order to accomplish this assistance these agents will interact with the user and with other agents representing the available travel services. The agent system is responsible for the configuration and delivery -- at the right time, cost, QoS, and appropriate security and privacy measures -- of trip planning and guidance services (e.g. multimodal route planning, hotel and parking-lot reservations, individualised traffic guidance, tourism, plane reservation, metro guidance). Further, there is interaction with other supporting agents such as media agents, directory services (yellow and white pages), and information brokers that seek, evaluate, and deliberate on information.
For travel services to be available in an open and free market economy, it is crucial that the agents of different vendors be interoperable. An initial framework for this end will be accomplished by the FIPA standardisation initiative.
4.3.2 Description and Reference Model
The PTA system should support the following functionalities:
The reference model for the PTA application is introduced next. User devices, example services and expected communications means are discussed. Finally, expected agent types are listed.
Terminal
The user accesses the PTA System via software running on a variety of standard end-user computing devices (called PTA Devices). These may typically be:
Interaction among these devices may be desirable.
Travel services
A variety of travel services (called PTA Services) are integrated into the system by travel service agents (TSA's) establishing a common "front-end" for automated access to these services. Examples of such services are:
Communication
A variety of communication services are available for relaying information and data between the PTA devices, PTA services and user:
Not all methods of communication are always accessible and their availability can change during different phases of the trip.
The following gives the general reference model for a PTA system.
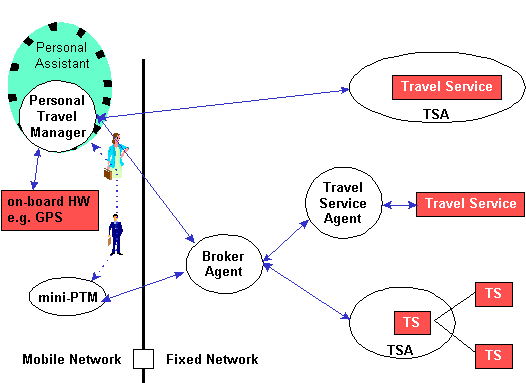
Fig. 2 - PTA Reference Model
Summary of Agent Types
4.4 Audio/Visual Entertainment and Broadcasting
4.4.1 Rationale
The expansion of digital broadcasting is expected to transform conventional television and radio into multi-functional, high-quality, and multi-channel systems and enable the provision of a wide variety of new information services. A vast amount of multimedia information is produced on a daily basis and browsing through 500 plus programs is no longer realistic or desirable. This offers potential markets for new businesses, and test-beds for agent-based systems to be used as filtering-retrieval-and-presentation component based on the user preferences. On the other hand, program production itself has to adapt to this new way of using and selecting the information. Furthermore, agent technology can increase the quality of the produced programs by allowing special kind of processing (e.g. object tracking).
Therefore, the application scenario described here consists of a Production Studio connected to the Receiver (User) side over a network. Autonomy and Intelligence is expected to be in both sides in order to support more functionalities that agent components are able to provide in a more efficient way.
4.4.2 Description and reference model
The production of a multi-media program in a studio can eventually benefit of the agent technology as here described.
A Camera-Tracking Agent handles the video streams, coming at real time rates from a number of cameras, to be combined within a production environment, for example for mixing, then composited with other elements, e.g. synthetic scenes, to form a sequence which is then broadcast live or stored for post production. The functionalities required from the cameras is simply the visual representation of the real world as seen by the eye. This electronic recreation of the world could be transmitted to another point in space or used to extract some useful information, such as an object to be tracked in the scene, or the position of the camera itself. Such a camera/vision agent may implement functionalities such as: 2D video manipulations, e.g. mixing and fading, object extraction/chroma keying and feature extraction. It may add value to applications such as TV production live/pre-recorded, virtual studio, enhanced reality, teleconferencing, cooperative working, and shared Virtual Reality.
Of course, this kind of functionalities should be implemented and synchronized also in the audio part of the system to provide a fully-integrated production.
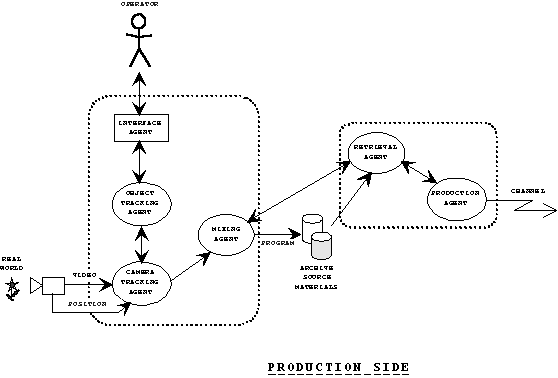
Fig. 3: Production Side
Production agents support program production by providing information to the user agents through the broadcasting networks. They can be used as production supporters which retrieve the bulk of information from the video archives located at the studios or from other databases in networks. They could provide the production staff with the required information to support program production. The information comprises video images and other data needed for the entire production procedure, from planning and shooting to editing (post-production).
They can also be used as communicators for exchanging information with other agents, in particular with user agents, to provide feedback and user reactions to new program productions.
This multi-agent system can be seen as an add-on to the structure of the set-top-box receiver that is proposed by other groups, e. g. DAVIC. Its main function is to assist the user in gathering information from incoming TV programs and from other networks (i.e. Internet), and then eventually store information users may be interested on. Therefore, capability to control digital storage media (e.g. VCR) at the user's home could be also integrated.
The agent-based entertainment assistant evaluates the service information of the actual
programs. These Service Information (SI), as defined in DVB (Digital Video Broadcasting) or
DAB (Digital Audio Broadcasting) and ATSC (Advanced Television Systems Committee),
includes information representing contents of the program like basic program-service label
(i.e. the name of a program service), program-type label (i.e. news, sports, classical music,
etc.), more detailed contents description (i.e. keywords, sentences with parsed tree, logical
form, etc.), etc. These are evaluated to create, on the basis of the knowledge of the
preferences and the habits of the viewer/listener, a list of possible films/channels (Personal
Electronic Program Guide).
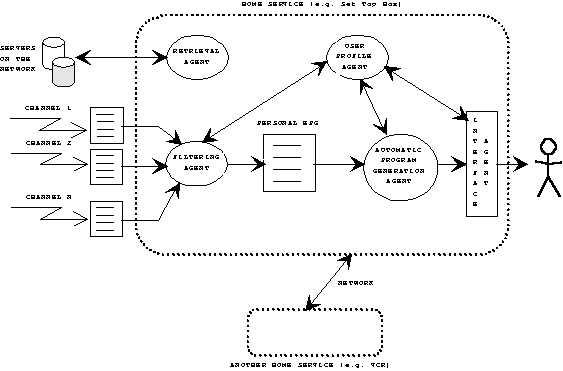
Fig. 4 - Receiver Side
The Retrieval Agent is also autonomously able to access other information providers and start a retrieval for a desired purpose (e.g. Video On Demand Server, Internet, etc.).
User profile/interface agents must possess ability for autonomous learning of the user's profile (i.e. the likes and dislikes of the user) and to provide a personal friendly interface to the user interaction with the system (e.g. natural language, text-to-speech, ...).
The multi-agent system is expected to survey automatically detailed background information of ongoing programs at the user's request. For instance, if the user asks for further information about a program, it will provide names, and detailed information about actors and more.
An automatic program generation agent is also part of the expected scenario. It should have
the capability to personalize and produce unique programs for that user by manipulating the
incoming information by super-imposing sub-titles, music, changing objects in the scene, ...
Again, all this kind of manipulation should be done according to the User Profile that is
updated, day-by-day, by the User Profile Agent.
4.5 Network Provisioning and Management
4.5.1 Rationale
The applications described here form a cluster in the domain of network and service layer management. It has been recognized that this is a large and complex domain, and so a focused set of applications, that could benefit from the use of agent technology in the near-medium term, has been chosen.
The question then arises as to the benefits of agent technologies in this domain. Agents will be autonomous and adaptive. These capabilities allow for easier and more robust implementation of network management actions across boundaries, be they layers in the TMN (Telecommunications Management Network) models of ITU-T, or boundaries between networks and network management domains. In practical terms, the ease of implementation is due to a paradigm shift in which the locus of control and the architectural knowledge of the environment moves from the global platform, as determined by current standards, to a local authority: the agent. It is possible that these agents start with a only basic set of assumptions, then add to their knowledge throughout their lifecycle.
The application cluster area is described below from two perspectives. The first is a mapping of agents to the most well known architectural model of network management, the TMN model, possible applications and their relationship to the agents in the model are described. The second perspective focuses on the general properties of agents in the model.
4.5.2 Description and Reference Model
Agents may correspond to management activities currently found in many places in the TMN model. TMN presents a layered view of management. It comprises four layers, ranging from the management of individual physical elements to the management driven by the business processes. In practice a TMN managed network is not alone in the world, but may be connected to other networks, TMN managed or not, perhaps belonging to a competitor. In addition, as the sophistication of private networks increases, and home networks become commonplace, agent technology may be essential to deliver management services.
Another aspect orthogonal to the layered view, and not shown in the figure below, is the dissection of management into functions: fault management, performance management, accounting, etc. While these concepts from the model are valid and useful abstractions, they create numerous boundaries that, in any given implementation, are crossed by standardized function calls, protocols, procedures, etc. With the use of agent technology, we foresee implementation strategies which alleviate many of these problems. Agent based implementations will be more robust to change, and allow for interworking between networks with different management models, and of different scales.
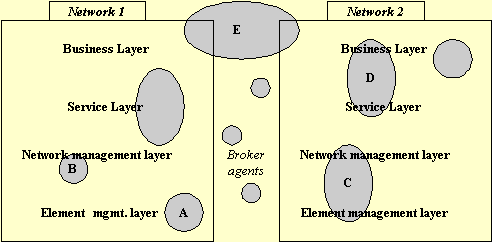
Fig. 5 - Mapping of agents to TMN layers
In the figure above, example agents, or agent clusters, and their mapping onto the TMN environment are shown. The figure shows only two networks, but the principles apply to interactions amongst many networks. All agents belong to some authority. The agents in the area between the two networks above could be owned by the network operator, jointly owned by multiple operators, or owned by a third party. Below we summarize the functionality of the example agents in the figure, labeled A through E:
The concept of network management agents is most powerfully described by a 'flat agent model', which means that no pre-determined fixed relationships between agents is presumed. Agents operate by providing services to each other in a non pre-determined way. Agents can:
Agents have a notion of acquaintances, i.e. other agents which can perform actions that the agent requires to fulfill its own purposes and meet its obligations. It is this relationship that determines the distribution of actions. It should be noted that such relationships, and hence the distribution of tasks, may change over time. Thus the agent model itself is flat, but it contains knowledge located inside the agents, that will create a structure. Note that the power of this model is that it allows interworking of management between many types of networks, with different hierarchies determined by the type of network management model, e.g. TINA, Internet or a small home network.
To be able to function in such an environment an agent has to have certain domain information and capabilities. These include:
5. Technologies requested by this Call for Proposals
5.1 Introduction
This chapter presents the essence of this Call. The following three sections describe the areas of technology proposed for specification in 1997, including descriptions, examples and criteria for each.
Each section also refers to additional enabling technologies which are not candidates for standardisation in 1997 but may be required to implement the target applications.
Any examples and reference solutions given in this chapter are for clarification. FIPA neither
requires them nor endorses them for use in this Call for Proposals.
5.2 Agent management
5.2.1 Introduction
This section addresses the issue of managing agents in a system. An agent system can be much less structured than hardwired or pre-defined systems. However, there is a need to have standards describing how the knowledge about the system -- and agents therein -- is conveyed to other agents and to a human operator configuring and managing the system. The call for techniques in this section addresses the minimum amount of technology deemed necessary by FIPA to allow agent to cooperate in a system in a sensible and efficient way and, thus, ensure interoperability among agents. Examples of technologies mentioned in this section are for purposes of focus only, and not in any way deemed normative.
5.2.2 Agent Interface Description Language (AIDL)
Description
Language that describes how to identify, access and interact with an agent. Used by agents to locate, identify and access other agents which may be helpful to fulfill their purposes. This language should be used by agents to describe themselves to other agents, and can be used internally to represent a model of other known agents (i.e. acquaintance model). AIDL expressions may be interchanged in messages between agents (cf. Section 5.3).
Example
An agent may look for another agent which is capable of performing a specific task using a query expressed in AIDL.
Criteria:
5.2.3 Agent Security
Description
A security model for agent interaction with each other and with their environment (i.e. user, SW and HW).
Example
A travel agent needs to prove its identity and authorisation to make a reservation with a service on behalf of its user. After making the reservation, it can not deny having made it.
Criteria
Enabling Technologies
Security in the underlying communication network is not addressed by this call, and is
considered to be an available enabling technology.
5.2.4 Agent Lifecycle Model
Description
A model which allows for creation, modification, migration, and deletion of agents in a system. This allows for the management of a system with agents and gives the framework for agents in the system. The model may incorporate several different lifecycles, depending on the particular system requirements.
Example
Upon creation an agent announces its description (in AIDL) to relevant parties, does its work, and notifies relevant parties before leaving the system.
Criteria
5.3 Human/agent and agent/agent communication
5.3.1 Introduction
Agents need to interact both with other agents, and with humans. There is a significant overlap in the requirements for both agent to agent, and agent to human interaction, so FIPA believes that there is enough commonality to consider attempting to meet both sets of requirements with one technology. The categories of messages that are exchanged, and the higher level structures of the dialogue, could be viewed as essentially the same in both cases. The dialogue with the human will need extra layers of translation to be understandable by both parties. We also recognise that, while agent interactions are modeled on human to human interactions, the current state of the art in computationally recreating these interactions may mean that agent only protocols are simpler than their human counterparts.
To ensure that independently developed, heterogeneous agents are able to communicate effectively, a precise syntax and precise semantics for messages is essential. The semantics of the messages should be expressed formally.
Cooperation and coordination are basic common behaviours in both agent to agent, and agent to human interaction. FIPA requires common protocols which are flexible enough to allow different types of cooperation. The execution of these protocols is dependent on, and possibly controlled by, the interpretation by the agent of currently expressed intentions.
Standardised interaction arises from correctly executing shared communication protocols. In the following text we consider a protocol to be a collection of messages that will be exchanged by the parties in the interaction, together with the rules, constraints and additional semantics that govern the various sequences of exchanged messages, and the meaning the agents should derive from them. We adopt the view that a protocol is more useful when viewed more as a dynamic, flexible entity emerging from the actions that agents take in response to messages and able to change in response to changes in the environment, rather than a stable, predetermined script.
To support this view we also adopt a design stance with respect to the conceptual design of the protocol, without prejudicing the choice of any given implementation. In this design stance, we view messages as self-contained abstract entities, and as the primitives in the construction of protocols. The semantics of messages then are defined locally to that message, and semantic expressions that are functions of multiple messages (e.g. the expected reply to a given message) are specified in the protocol. A given message then, could be used in the definition of multiple different protocols.
5.3.2 Message types
Description
The message types should correspond not only to primitive communicative acts (e.g. request, inform, confirm, etc.), but also to complex combinations (e.g. sequences, alternatives) required by the negotiation and coordination protocols used by the agents.
Examples
Criteria
5.3.3 Message contents
Description
The content of the message is the argument to the communication act specified above. The actual message content description formalism is an implementation choice. However, to facilitate communication, the content must be accessible in a general way. Characteristics of the content, such as the ontology and encoding scheme, are available in a standard.
Examples
A user requests the agent to reserve a seat on a plane. The content of the message must allow the representation, in general way, of a domain action from the ontology, and other domain specific information. In this example, the action is "reserve", and the domain information is "a seat on a plane" (a formula with a free variable).
A user asks the AV-entertainment/broadcast agent the scores of the baseball games today. The agent informs the user that there was no game today. The answer is a quantified formula ("there was no game").
Criteria
5.3.4 Interaction protocols
Description
Agents can enter into negotiation or cooperation processes with other agents or humans. These processes vary in complexity, from simple handshaking, through cooperative task achievement to complex negotiation and trading exchanges. At one time, an agent may be engaged in several overlapping interactions for the purpose of attaining a particular goal.
Protocols are implemented through the exchange of messages, but they impose constraints and expectations on the way that the agents behave with respect to the other agents or humans in the interaction. Simple human-agent protocols may be accomplished as directive dialogues, in which the set of responses expected from the human is indicated through the interface.
The protocols for these interactions can be specified at different levels. At one level, we specify the kinds of response we expect in reply to certain communication acts: for example, a question is followed by an answer. At another level, we can view the protocol as creating intentions and obligations in the parties to the interaction, for example the intention to reply to a request, or the intention to be cooperative and helpful. These intentions may or may not be explicitly encoded in the agent.
By agreeing to be bound by a given protocol, an agent is required to act in a given way. For example, an agent which declares itself to be cooperative will then be expected to generate cooperative responses, such as answers which are over-informative, corrective, suggestive, etc.
Interaction protocols may imply a number of different models for the delivery of messages to other agents or users. For example, point-to-point, multi-casting, broadcasting, etc.
Interactions controlled by a protocol may persist over varying periods of time, e.g. a agent may be required to commit to performing some action or actions at a later time. The protocol gives a framework in which different characteristics may change dynamically. An example would be: an agent must drop a commitment if the goal it was committed to is no longer relevant.
Examples
Criteria
5.3.5 Enabling technologies
5.4 Agent/software interaction
5.4.1 Introduction
Agents do not exist in a vacuum. In order to support an open and interoperable set of standards, it is necessary for FIPA-compliant agents to adapt to existing and future applications, services and devices. Furthermore, to support the agent-designer in constructing a FIPA agent it is also advisable to standardize how toolbox / component software should be integrated into the internal agent architecture. Each of these presents special requirements and will be dealt with in turn below. FIPA believes that both of these are fundamentally important in pioneering an open component market.
The following call contains two major requests for technologies: attachment to external applications and inclusion of (internal) cooperative software components. Every existing agent application has to date implemented some notions of the application attachment; many have also combined internal software components to varying degrees. It is not the expected result of this call to select one specific technique: neither to define the nature of component technologies, nor any specific internal agent execution architecture. FIPA solutions will be combined and refined into a set of protocols during 1997.
5.4.2 Attachment to external software, applications and services
Description
To enable an agent to attach to external software systems. This requires that both a computational and an informational description of the service exist together with necessary functions (in the external agent infrastructure) to attach the agent to the service. The working metaphor is to provide the "eyes, ears and hands" of the agent.
In its broadest sense, the same mechanism of direct attachment to devices is also applicable to the attachment to services. For instance, locating potential services, obtaining a description of these potential services, connecting and supporting the lifetime of these connections.
Example
Connecting an agent to a video server (e.g. DSM) for the purpose of filtering information. The agent needs to be able to locate a video server of the required type by referring to a suitable semantic description. It must be able to perform a filtering operation on the located server based on the stream / symbolic attributes of the media. There should be a set of support services available to maintain the integrity of the connection, for example, the agent responding to error or event-notifications.
Criteria
The interface within the agent to external applications should contain the minimum following set of features:
Description
To enable the inclusion and peer-to-peer coordination between internal software components. This interface will probably be similar to way in which the external interface attaches the agent core to applications. In the internal case, the interface attaches parts of the agent core to each other. On the other hand, dissimilarities essentially arise from the fact that the relationships between these internal software components are peer-to-peer and will require knowledge-sharing and possibly blackboard techniques.
Example
An agent designer wishes to construct a network planning agent using standard application components. In this case the agent might well include two components: a neural-network learning component which can provide predictions of traffic levels; and an operations-research algorithm which can dimension a network given a set of traffic models and constraints. The agent core provides standard interfaces to enable the straightforward inclusion of these components and for the sharing of information between them.
Criteria
The following criteria are concerned with the interface within the agent core to included software components:
The unification of software components within the agent core is provided by a task architecture. The nature and implementation of this task architecture is not the subject of standardization.
5.4.4 Enabling Technologies
The following technologies deserve consideration for the realization of the interfaces.
6. Example applications made possible by FIPA 1997 specification
6.1 Introduction
As an aid to those who will propose technologies the following paragraphs provide examples based on the scope of the four selected applications made possible by the availability of FIPA 1997 specification. It should be noted that by utilising the FIPA 1997 specification new and innovative applications can be brought to market.
FIPA is open to receive recommendations on how other applications or services might be served by this Call for Proposal and possible future calls made by FIPA.
A personal assistant is a software agent that acts semi-autonomously for and on behalf of a user, modeling the interest of the user and provide services to user or other people/PAs as and when required. For 1997 the intention is to construct a PA with a limited set of functionalities, using the FIPA specified technologies, as follows :
To illustrate some of the above characteristics a small application is outlined below.
An e-mail request for a meeting is received by the userís PA from an important customer, while the user is away from his desk. The agent notifies the user by GSM phone, using a text-to-speech conversion service to convey the message to him. For the meeting the user engages in a dialogue with the PA requesting that the agent sets up the meeting with a number of participants (e.g., finding out a convenient time frame and an appropriate location). This would involve the meeting scheduling and directory services of the PA.
As a preparation for the meeting a multi-media document is to be forwarded to each of the
participants. Due to differences in the computer equipment, available to each participant, there
is a need for conversion of the document (or parts there of) to formats like text (i.e. leaving
out pictures etc.), so that comprehensible information becomes available to each participant.
In addition some users have only shared access to multi-media facilities and these users must
be notified of the information to be delivered. When appropriate network information is
available the notification might include a specification of the location of the closest vacant
multi-media facility (i.e., a Multi-Media PC) that will enable them to read the document. The
agent is expected to initiate all these services. For the people unavailable, the agent will try to
negotiate an arrangement with the corresponding personal user agents. In the event of failure
or problems the agent will either have to return to the user for assistance or determine
alternative actions.
6.3 Personal Travel Assistance
The agent standards established by FIPA in 1997 will enable the development of a first prototype of a fully functional PTA system. User input to the PTM and mini-PTM may be restricted to form-based textual input. Likewise, agent output to the user may be restricted to graphics and image display. Connection to existing travel services with defined API's and text-based interfaces (e.g. HTTP/HTML-based services) will be possible.
An example 1997 application of PTA is as follows:
A user queries a "personal assistant" (running on a portable device or on a personal computer) using natural language (voice recognition and/or typed text):
"I must meet M. Kane of Rosebud company in New York in the afternoon of the 29th of September. Plan me a trip for this appointment. I would like an answer by tomorrow evening, take my standard preferences into account."
The system is expected to take, at a minimum, the following actions:
6.4 Audio/Visual Entertainment and Broadcasting
6.4.1 Overview
The need for information filtering and retrieval is necessary, in particular for digital broadcasting networks. The selection and storage of one's favorite choice from the great many programs on offer is practically impossible. The information has to be provided in a customized manner to suit a user's personal preferences (Profile). In order to implement the information filtering and retrieval, the semantic and syntactic content of the broadcasting data streams need to be made compatible to provide a consistent method for selection. It is important that the human interaction with the system must be "user friendly" by providing an intuitive human-system interface. These functionalities such as profiling, filtering and retrieving, and interfacing can be reinforced by introducing agent technologies. The possible applications that require these functionalities are: TV Broadcasting, Radio Broadcasting, Data Broadcasting (e.g., Weather forecasting, Stock Market Price), Electronic Newspaper, Commercial Database Service, Internet Service, Computer Aided Education, Video- and Multimedia-on-Demand Service, Entertainment, Home Automation, and so on.
The identified necessity for this application is as follows:
This application consists of the following three types of agents:
Interface Agent
Profile Agent
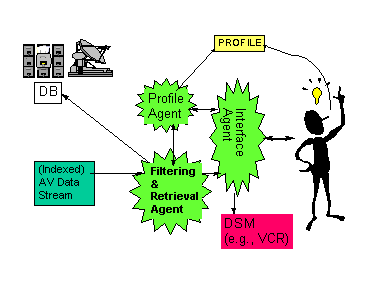
6.5 Network management/provisioning
6.5.1 Introduction and Context
The following applications and their detailed descriptions are offered as examples of network provisioning and management applications that FIPA specifications will enable in 1997. They are chosen with recognition that they are useful, practical and that ongoing research and development exists which may fulfill some of their requirements and functionality. It should be noted that agents implemented from FIPA specifications are intended to exist within the context of ongoing network management technologies and standards initiatives, such as TMN and TINA. Agent technologies are intended to complement such activities by providing technological support to the computational and knowledge level tasks of integrating and coordinating applications and software components in an open-ended manner.
6.5.2 Application: Service provisioning, activation and resource allocation
The agent (or collection of agents) assists in the elicitation and fulfillment of customer requests for network services. These may take many forms: a large corporation constructing a corporate intranet, a cable-TV operator connecting a new home installation, to a consumer purchasing a home communication appliance from a retail point of sale, which needs to be connected to the home network and hence to the wider network.
These activities take place in the context of the operator's business model. The agent (D in
Fig. 5), spans the business layer and the service layer. Typical steps in the process are shown
below:
| Business model step | Corresponding detailed activities |
| Process customer request | Receive and refine the customer request Verify customer identity Match customer requirements to service offerings |
| Assist in the planning of network resource needs | Develop service profile Check customer request against business rules Check resource availability (check service layer) Schedule supplementary investigations (e.g. survey CPE) Assess legal and regulatory implications |
| Confirm feasibility of customer request | Verify customer credit background Create service contract Obtain authenticated commitment from customer Enter into binding agreement |
| Activate the service | Determine network provisioning parameters Construct monitoring framework Activate billing Allocate network resources Activate customer care Turn on service |
| Service monitoring | Confirm compliance to service contract (network
operator and customer) Initiate obligations on network management agents. Execute customer care procedures |
| Service re-negotiation | Respond to customer requests for service extension, or
detect circumstances requiring service contract
modification Enter into negotiation with customer Modify or terminate service accordingly |
| Service termination | Detect attainment of service termination criteria, or
respond to customer request to end service Remove obligations on other agents for this service Ensure that termination procedures are completed and resources freed |
6.5.3 Application: Remote Autonomous Element Management
The agent (or collection of agents) perform a full spectrum of network element management and monitoring services. Considerable latitude is granted for the agent(s) to undertake autonomous actions both to respond to network fault conditions and to apply preventative measures. Many different networks may benefit from this agent-oriented approach: telephony, satellite, broadband video, wireless, etc.
These activities take place primarily in the context of the operator's network management operation. The agent (A in Fig. 5), operates primarily in the element management layer, but will require considerable interaction with entities in other layers. Typical steps in the process are shown below:
| Business model step | Corresponding detailed activities |
| Configuration Management | Agent maintains inventory of network element(s) it oversees and sets state of network and element configuration parameters. Agent processes requests from other entities (after verifying their authority) to set or modify network element configuration parameters. Agent upgrades operational software of network element(s) it oversees. |
| Performance Management | Agent monitors network element performance parameters including, as appropriate, end-to-end system-level factors. Agent reports to appropriate entities when performance is outside of accepted levels. Agent takes action within its authority profile to attempt correction of the performance violation. |
| Fault (Alarm) Processing, Filtering and Correlation | Agent monitors alarm conditions of all network elements it oversees. If one or more alarms are detected, agent applies filtering profile to determine severity of the alarm(s). Agent correlates alarms to identify root causes and classifies these according to severity. Based on its authority profile, agent takes autonomous action to correct alarms |
| Escalation of Fault (Alarm) or Performance Violations | If alarms occur which require corrective action that is outside of the agent's authority profile, agent contacts appropriate escalation entity and reports fault condition(s). Agent executes instructions of escalation entity. If agent detects performance violations which are outside of the agent's authority profile, agent contacts appropriate escalation entity and reports performance violation and executes instructions of the escalation entity. |
| Preventative Actions and Network Health Maintenance | Agent monitors selected network element and performance parameters to identify trends which may signal impending element or network failure. Agent determines whether impending failure can be prevented and applies appropriate correction (within its authority profile). If correction requires external entity, agent contacts appropriate entity and informs it of the possible impending network failure. Agent executes instructions of the external entity. |
| Security Management | Agent verifies integrity of all messages it receives and provides a basis for integrity verification of its own messages. Agent periodically checks software integrity of network elements it oversees. Agent also periodically checks its own software integrity. Agents maintains log of illegal requests made by external entities. |
| Status Reporting | As part of normal operation, agent reports status of network element operation, agent operation and other parameters in its reporting profile. |
6.5.4 Application: Federated Customer Care
The agent (or collection of agents) assists in the elicitation and fulfillment of customer care requests. These could involve such examples as: a small business experiencing telephony service problems, a home video services subscriber with a billing problem or a large Internet Service Provider experiencing routing problems in connections to a backbone network.
These activities take place primarily in the context of the operator's business model, but will
involve contact with entities within other layers, domains or networks. The agent (E in Fig. 5),
spans the business layer and the service layer. Typical steps in the process are shown below:
| Business model step | Corresponding detailed activities |
| Receive customer care request | Gather, refine and record elements of customer care request. Respond to customer with confirmation of care request reception and acknowledgment. |
| Process customer care request | Verify account status of customer. Determine nature of customer care needs and identify networks, domains and layers which may be required in solution. Determine performance criteria (time, cost, etc.) for acceptable resolution of customer request. |
| Arrange service contract with other networks, if necessary. | Agent sends service contract request and processes responses. If negative response is received, agent investigates further and issues modified service contract request to achieve resolution. |
| Initiate customer care response | Agent contacts all entities required in the customer care solution and dispatches appropriate service requests. Agent takes appropriate actions within its domain of authority as part of solution. Agents confirms that all required entities accept service contracts. |
| Monitor progress of customer solution | Agent monitors all entities involved in the customer care solution to verify that services contracted for are executed properly. Agent reports on progress of solution to customer and appropriate network personnel and maintains a log of the progress of the customer care solution. Agent makes determination of completion status of customer care solution. |
| Escalation of customer care request | Agent monitors progress of care solution and determines if performance criteria have been exceeded. If performance criteria have been exceeded, agent contacts appropriate escalation authority. Agent performs instructions received from escalation authority. |
| Close-out of customer care request | Agent verifies that all requirements of customer care solution have been met. Agent closes all open service contracts and reports to customer and appropriate network personnel that care request has been satisfied. Agent archives records of customer care solution activity. |
Those intending to submit a proposal(s) should take note of the following important information.
1. Notify their intention to submit a proposal on or before 31 December 1996 to:
| Dr. Leonardo Chiariglione | Tel.: +39 11 228 6120 |
| Multimedia and Video Services | Fax: +39 11 228 6299 |
| CSELT | Email: leonardo.chiariglione@cselt.it |
| Via G. Reiss Romoli, 274 | URL: http://www.cselt.it/fipa |
| I-10148 Torino | |
| Italy |
2. Submit their proposal in electronic form, MS Word (V6.0x) or HTML (the latter is preferred) by 10 January 1997 to the address shown immediately above.
3. Bring 100 copies of their proposals to the 4th meeting in Torino, Italy.
4. Attend the meeting on 20-24 January 1997. Additionally, proponents should be prepared with visual aids for a brief (15 minutes) presentation of their proposal in the event it is requested.
In the submission the proponent should
Proponents should be aware that all material presented to FIPA shall be deemed of a
non-confidential nature and hence will be made available to FIPA members and participants
in the January '97 meeting. Proposals received will be posted on the FIPA home page and
will be made accessible for consultation by FIPA members.