Figure 1. Stucture of BIFA
Ari Widodo |
Takaaki Hasegawa |
Saitama Univ. Dept. Electrical and Electronic System Eng.
255, Shimookubo, Urawa-Shi, Saitama 338, JAPAN
In multimedia communication services like Internet or Intranet, the network traffic's load becomes huge because of transferring multimedia data, such as movie and sound data. Such conditions, require a large capacity of line. To improve the efficiency of using line and the quality of communication, we propose business trip information filtering (BIFA). BIFA is an agent which performs information filtering at a server that as network load is reduced. In addition in this proposal we propose some interfaces which are used in BIFA to communicate with external software, applications and services.
In multimedia communication services like Internet, the transfers of multimedia data like movie, pictures and sound data frequently occur. In these communication services, transferred data often exceed the maximum requirement. Therefore the network traffic's load becomes bigger and the quality of communication becomes worst. These two things have been a serious problem to be solved.
Recently, there are two methods of information filtering on the network. First, in receiver people or software will do these jobs. Second, by using a proxy server located between transmitter and receiver. A weakness of this method is heavy loading of the proxy server which causes delay for receivers and reliability of the proxy server. In addition, all of the uses cannot always use proxy servers; this situation makes the network's load high.
To solve these problems we propose the business trip information filtering agent (BIFA). In this system, the receiver (henceforth called "user") send an agent having a list of needed information with its version to the transmitter (henceforth called "server"). When the server has requested information whose version is newer that the agent (the user) has, the request is accepted and then transferred automatically to the user. It means the information transfer has been filtered. Therefore, the network traffic's load can be reduced. Also, the proxy server's problem does not occur.
BIFA consists of two different agents. The main agent is called "BIFA" and the sub agent is called "SUB BIFA." BIFA always exists but SUB BIFA is created when the communication is needed and is deleted if its mission is completed.
In this proposal we propose the BIFA's interface needed to communicate with other agents, external software, applications and services. First we will describe the function of BIFA. Next, we will also describe the structure of BIFA in network communication. By understanding these matters, we will explain the BIFA's interface. At the end of this proposal we will make conclusions. To complete and to support this proposal we also attach an appendix.
BIFA has some functions and they will be described below:
In this section, we describe information required and methods used BIFA to get information user's need.
2.2.1. Information required
2.2.2. Methods to get information user's need
After getting the user's need of information, BIFA creates SUB BIFA and then load these information to SUB BIFA. With these information SUB BIFA communicates and negotiates with server. Information that BIFA load into SUB BIFA are described below.

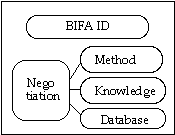
Figure 1. Stucture of BIFA
As shown in figure 1, BIFA has five elements in its structure. Those elements are described below.
SUB BIFA uses almost the same model as BIFA has, but there are still some differences between them.
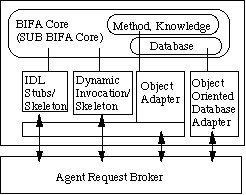
To describe the detail structures of BIFA and SUB BIFA, we use CORBA v.2.0 standard[1]. The detail structure can be seen in figure 2. From the figure, we can see that BIFA and SUB BIFA are independent agents above-mentioned the Agent Request Broker (ARB) [2]. Therefore BIFA and SUB BIFA has a flexibility which can be plug-in and plug-off. The interfaces shown at figure 2 will be explained in next chapter.
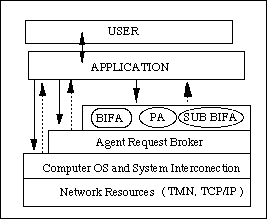
As communication platform we adopt the platform model that had been discussed on Telecommunication Information Network Architecture (TINA) workshop[3]. The location of BIFA and SUB BIFA at TINA's platform model can be seen in figure 3.
BIFA uses Agent Request Broker (ARB) to connect with other agents, software and user. Meanwhile to communicate with other networks communication, BIFA sends SUB BIFA through ARB, OS and network resources by using General Inter ORB Protocol (GIOP)[1]. At the network resources the SUB BIFA is mapped into network protocol that has been using. The detail explanation can be seen in appendix.
In this chapter we explain about BIFA's interface mentioned above. In this proposal we use Object Management Group Interface Definition Language (OMG-IDL)[1] to define these interfaces.
These commands and their paramater can be seen in table 1.
| COMMAND | PARAMETERS | SEMANTICS |
|---|---|---|
| GUIDE | Information list, help | Guidance for user by using GUI & API |
| ASK | Information ID, task ID | Make inquire to user |
| OPEN | Database ID | Open database that has been requested |
| CLOSE | Database ID | Close the active database |
| LIST | Information ID, Database ID | Make the information list into database |
| RECORD | Information ID, Database ID | Record a new information or database |
| CANCEL | Information ID, Database ID | Cancel the information from list or database |
| SHOW | Database ID | Show the database contents |
| RESET | Database ID | Reset the current database contents |
Exp. User wants to know about world news but what he wants is yesterday news. By using guide, the user tells the BIFA about it and BIFA make requested information list (database) and record it to BIFA's databases. And after BIFA's got the request information, BIFA shows it to the user, and the user can order to BIFA for deleting, resetting the database.
This interface is defined by IDL stubs and IDL skeletons of OMG-IDL.
These commands and their paramater can be seen in table 2.
| COMMAND | PARAMETERS | SEMANTICS |
|---|---|---|
| CREATE | Agent ID | Create SUB BIFA agent |
| DELETE | Agent ID | Delete SUB BIFA agent |
| SET | Database ID | Load database into others agents |
| GET | Database ID | Get database from other agents |
| ASK | Agent ID | Make inquire with other agents |
| LIST | Database ID | Make task list of new other agents |
| RECORD | Database ID | Record database to BIFA's databases |
| CANCEL | Agent ID, Database ID | Remove agent ID and its database |
| SEND | Agent ID | Send SUB BIFA to other systems |
| ACTION | Task ID | Negotiate with other agents |
Exp. gets the requested information from personal agent or travel agent (using commands: ASK, LIST, GET and ACTION). This information is loaded into SUB BIFA which BIFA creates (using commands: CREATE, SET, and ACTION) and send SUB BIFA to server (using commands: SEND). After the SUB BIFA completed its mission, it is deleted by BIFA (using command: DELETE, CANCEL).
This interface is defined by dynamic invocation and dynamic skeletons of OMG-IDL. SUB BIFA has only this interface to communicate with external software, applications and services.
These commands and their paramater can be seen in table 3.
| COMMAND | PARAMETERS | SEMANTICSL |
|---|---|---|
| ASK | Software ID | Monitoring the software condition |
| CONNECT | Software ID | Make connection with software using API |
| LIST | Information ID | Make requested information list |
| GET | Information ID, database ID | Get a single or prural requested information |
| SET | Information ID, database ID | Set information into software |
| RECORD | Software ID | Record a new software into BIFA's databases |
| ACTION | Task ID | Execute the software |
This interface is defined by dynamic invocation and dynamic skeletons of OMG-IDL.
In this proposal we do not propose Object Adapter's interface and Object Oriented Database Adapter's interface. These interfaces is taken from CORBA v.2.0[1].
In this chapter we will explain the working method of BIFA.
From all explanations mentioned above, the conclusions of this proposal is described as follows :
Reference:
In figure 4, we proposed the network communication protocol that used by BIFA.
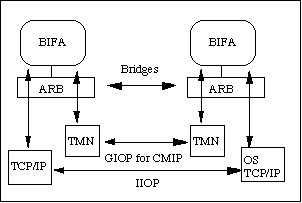
The detail explanation of these protocols is described below.
The content of command field as shown in figure 5 is AAI command. The information loaded in the parameter field are described below.
FIPA's First Call for Proposals