This paper discusses recommended technologies for use in the
implementation of intelligent agents in broadband networks. Specifically,
agents for use in network management applications are the prime
focus. Some of the technologies of interest are: object request
broker architectures, security algorithms and source code
portability.
Operators of broadband networks can benefit from agent technologies. As discussed in the First FIPA Call for Proposals, many aspects of network management can be improved with an agent approach. Having agents with autonomous capabilities can ameliorate the laborious and tedious tasks of network status monitoring and corrective response to fault conditions. Some of the network management functions an agent may assume are:
One of the fundamental tasks of a network management system is to monitor and track device alarms and report such alarms to the network operator. Current standard agents typically can discover and report on alarms, but do so simply by gathering and relaying information about the alarms to the operator, sometimes causing a flood of seemingly unrelated indications. In many cases, multiple alarms may all be related to one root cause and thus clearing the root alarm condition can also clear the subtending alarms. In any case, agent technologies could be applied to analyze such multi-alarm situations, and by using expert knowledge, correlate the individual alarms and identify the common fault condition.
If an agent can successfully analyze a complex set of cascaded alarms, it might also be possible to enable it to take action to clear the root-cause condition, thus also clearing the subtending alarms. Building the capability for autonomous action into a network management agent could have exceptionally positive effects on network availability, QoS and efficiency.
Likewise, agents could be constructed to constantly monitor network conditions and devices and take actions to prevent impending fault conditions.
Since many varieties of broadband networks may be inter-connected to form larger networks, interpretation and regulation of QoS at network boundaries and real-time protocol conversion and bandwidth metering could be tasks assigned to intelligent agents on the borders and points of presence of the network.
Many broadband networks must operate upon a resource sharing
principal. At different times, bandwidth, data rates, virtual channels
and other parameters must be re-allocated amongst different uses
and/or users. In many cases, the scheduling of these
re-allocations may be driven by a relatively manual process. A
master scheduling controller may be used to store information
about future network usage and then used to direct
sub-controllers to reconfigure network elements to carry out the
re-apportioning. Some example services which require advanced
provisioning and resource allocation are: Video-On-Demand (VOD),
Near Video-On-Demand (NVOD), bandwidth management, data communications management,
network element configuration, address assignment and switching
management. Agent technology can be applied in these domains.
This section offers recommendations for tools and mechanisms for implementing some of the important characteristics, capabilities and features required to enable agents in broadband networks.
The agent must be implemented in a platform-independent manner. This means using a programming language and/or model that allows an implementation of an agent to be installed and run in many different hardware/software operating environments with little need for modification to the agent. Concepts such as "virtual machines", "p-code", "byte-code" and the like are useful paradigms for achieving such independence. Clearly the JavaTM programming language should be considered as the primary contender for a tool in this area.
Agents should be structured so that they are able to perform their functions in the presence of numerous network protocols. The agent should be able to automatically adapt to different networking protocols or at least be adaptable through manually-selected dynamic linking of different network drivers without requiring re-coding, re-compiling or other special handling. However, certain standards regarding network management are so well-established that effective agents will have to consider and perhaps adopt them. These standards are the SNMP and CMIP/CMISE protocols/models. Also, DSM-CC or ISO/IEC 13818-6 should be considered when multimedia session connectivity is called for.
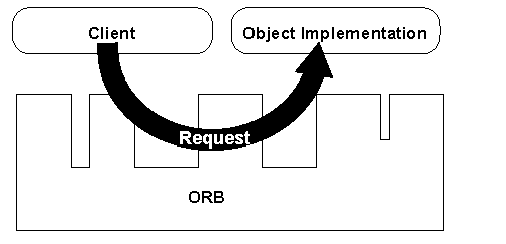
Because agents are largely asked to deal with real-world elements and concepts, producing an agent using an object-oriented approach is not only a convenience, but a necessity. Object-oriented approaches also tend to support the kind of extensibility and metamorphosis that advanced agents will require over time. Since agents will often be found in high availability tasks in broadband networks, the re-use of code and related elimination of the re-testing burden that properly implemented objects can provide, would be a welcome attribute of agent approaches. It is recommended that to meet these requirements the CORBA Revision 2.0 (July 1995) specification be followed. In particular, OMG IDL syntax and semantics should be adopted for defining agent interfaces within the object architecture. The basic CORBA model is shown in the figure below:

Clients make requests through an object request broker to obtain access to objects of interest. This model is particularly useful in networked applications due to the excellent degree of abstraction it provides for the interface between agents.
Agents may be deployed in applications in which funds transfer, purchase, network integrity, power management and other sensitive factors are at stake. It goes without saying that strict security measures must be applied to the actions of these agents. This includes agent authentication, message integrity, message privacy and agent integrity (anti-virus) considerations. To provide these services, it is recommended that strong cryptographic techniques be employed. In particular, the RSA public/private key algorithm and digital signature protocols should be used for authentication, message integrity and agent integrity. For general messaging privacy, appropriate secret-key block ciphers may be chosen such as DES (NIST FIPS 46-2), Triple-DES (ANSI X9.17 and ISO 8732), etc. The basic difference between public/private key and secret key ciphers is shown in the figure below.
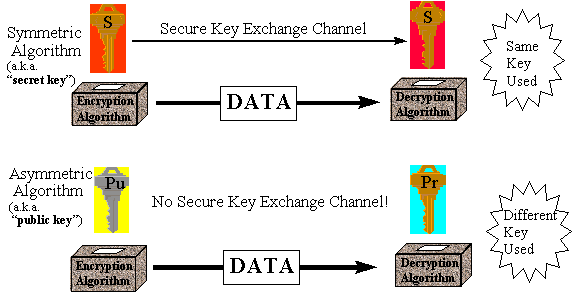
In a secret key algorithm, the encrypting key (S) is identical to the decrypting key and thus a secure key exchange channel is needed between entities performing these operations. In public key algorithms, the encrypting key (Pu) is different from the decrypting key (Pr), however, the two are uniquely related and work only with each other.
Other security protocols of interest to FIPA are:
For IP protocol implementations the following IETF "standards":
S-HTTP (Secure Hypertext Transfer Protocol, Internet draft: draft-ietf--wts--shttp--01.txt)
S/MIME (Secure Multipurpose Internet Mail Extensions)
SKIP (The Simple Key Exchange for Internet Protocols, Internet draft: draft--ietf-ipsec-skip-06.txt)
AH (Authentication Header (RFC 1826))
ESP (Encapsulating Security Payload (RFC 1827))
SSL (Secure Sockets Layer (Internet draft: draft-freier-ssl-version3-00.txt))
Other security-related standards:
ITU-T X.509 (Public key certificates)
SET (http://www.mastercard.com/set/set.htm, Secure Electronic Transactions for credit card commerce over the Internet)
PKCS (This Public Key Cryptography "Standard" is a Technical Note of RSA Laboratories. It serves as guidance to developers in the absence of existing standards for public key protocols)
IEEE P1363 (effort to create a balloted standard for public key techniques; first working draft released in August 1996; covers cryptographic primitives, data formats and protocols)
ISO 7816 (smart card mechanical, electrical and
protocols)
The rapid expansion of the exploitation of broadband networks of various types is contributing to the development of a global information economy that will support numerous new applications and services. The networks that carry these services will become more ubiquitous and complex and their configuration, management and operation will become increasingly daunting tasks. Intelligent agents can play an important role in enabling this expanded world. To do so in an efficient and cost-effective manner, standards are required. This paper has suggested some tools and mechanisms that may be appropriate for intelligent agent specifications.